7.2 Smart Distributed Resources (SDR) layer
Another layer that defines the XIDEN Blockchain is called Smart Distributed Resources (SDR). The SDR layer forms a network with a decentralized architecture and provides computing power and storage for all participants with smart electronic devices registered in the XIDEN network.
SDR is an eco-friendly concept as its implementation aims to bring together all devices that have or have had a utility for the owner user. In this system, the resource management is done automatically by the SDR layer in order to not affect the activity of the device and facilitate specific access to the respective device by the other users of the network.
Many devices such as smartphones, computers, or servers have become obsolete with the advancement of technology and operational requirements, and recycling them represents a difficult option. Thus, the SDR layer represents a solution for optimizing their utility by using their resources within the network and it will reward the owners with XDEN for making their resources available for the other users in the network.
Current up-to-date smart electronic devices are not being utilized at full capacity at all times, even though they maintain the same power consumption. Through the SDR layer, the owners will be incentivized for making their resources available to the network and this process will not affect their performance for regular activities in any way.
This concept empowers users to utilize their smart devices’ power in different areas. It represents a good thing as these devices use only a minimum level of their energy output to function for their intended purpose, and do not need special reconfiguration to be used on this blockchain.
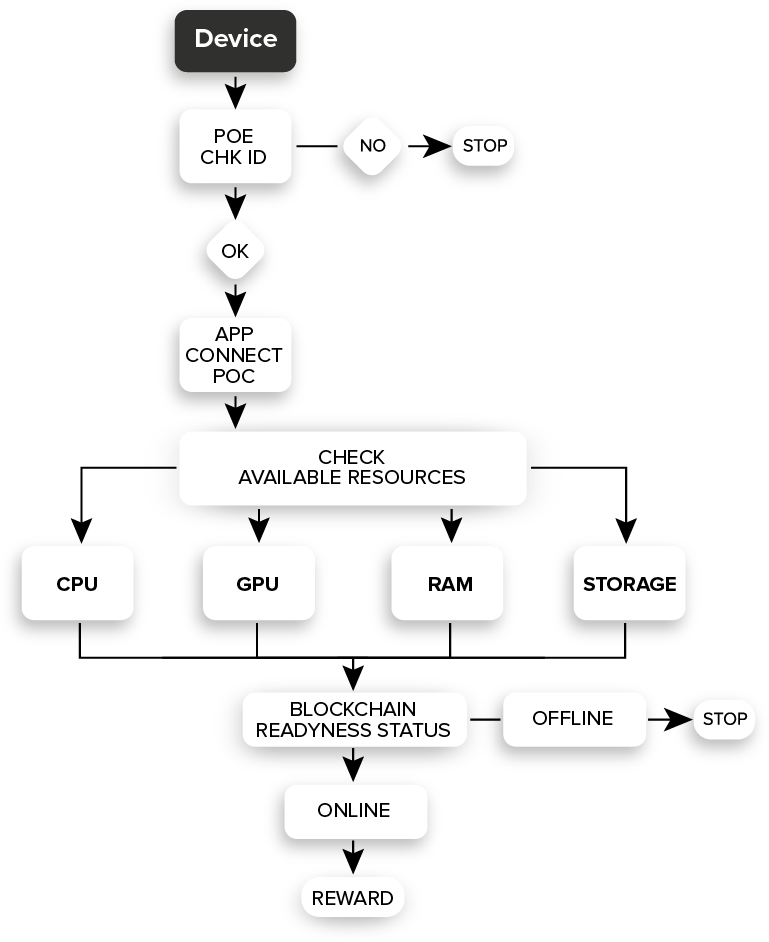
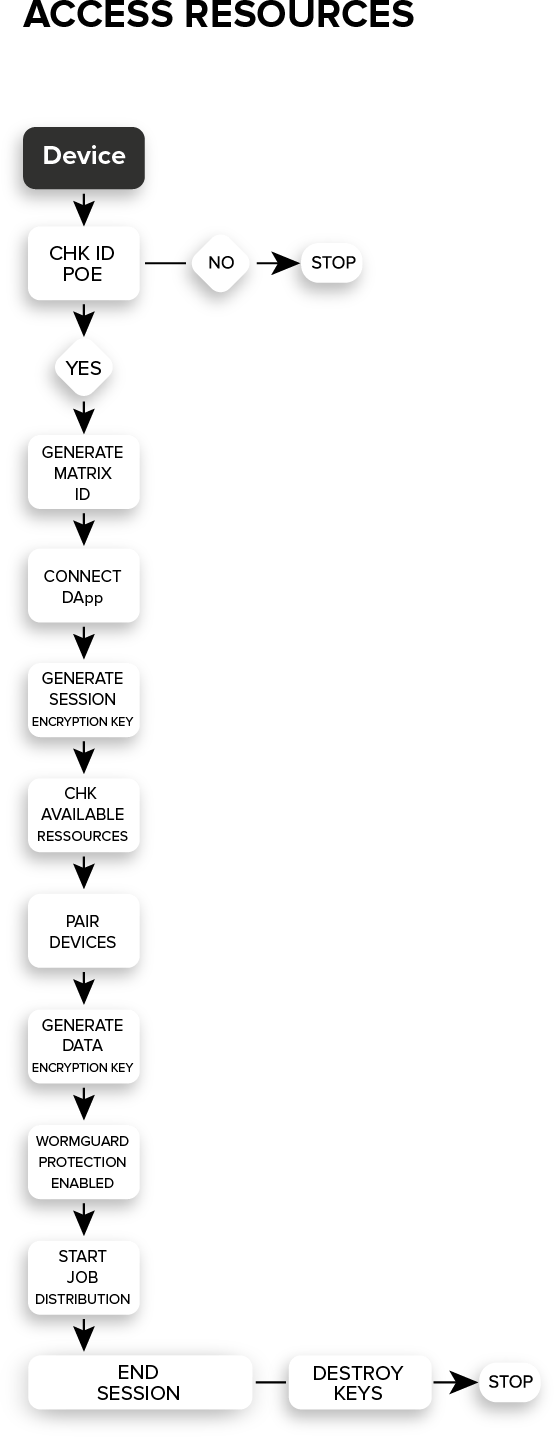
The most important part of the SDR layer is represented by the security provided for the devices integrated into the system. To connect to the XIDEN network, users must install the PAIR application for the XIDEN network. This application has Worm Guard installed by default, a system that protects devices from any unauthorized attack.
The application is an interface that only distributes computing or storage jobs to registered devices and does not allow system access or access to any other functions.
The compound of Proof of Staking (POS), Proof of Connectivity (POC), and Proof of Existence (POE) protect users from any attack. When an irregularity is identified by the three consensus layers or by the Worm Guard system, an ODI attempt or attack will be reported; The initiator of the attack will be isolated and punished by receiving burn for his amount of XDEN available in his staking supply. The three consensus algorithms work actively to maintain the integrity and security of devices and the functionality of the system.
Communication between the devices is P2P and is subject to the consensus rules. Each device uses a generated Matrix ID and does not use its actual identity to communicate. Data transfer uses the VOBP protocol when accessing the device’s resources, to encrypt and protect jobs. Being a decentralized network, privacy is extremely important and any task distributed to the network must be visible only for the user that initiated it. Session encryption keys will be generated for securing the channel and message encryption keys (JOB) will be generated for protecting the content. The storage protocol combines the operating architecture of torrents with the operating architecture of IPFS and organizes them in a decentralized manner.
The POE and POC consensus layers verify the validity and conformity of the devices integrated into the system. The storage information is disassembled in several parts through a unique process for each user. The parts are encrypted and sent to devices that have valid storage capacity. The same piece of information is stored in multiple devices ensuring access to the respective information at all times. Because one or more devices can go offline, the protocol constantly checks that the information is valid and available on a minimum number of devices. If it reaches the minimum number, then the information is replicated on another online device. These decentralized algorithms provide 100% uptime for network data.